Jun 10, 2021 By Team YoungWonks *
What is a Virtual Private Network? Before we get into this, let us imagine a scenario: a business enterprise has grown and now it needs its employees to work out of multiple offices across the city, town or even the world. To ensure that things are functioning smoothly in these offices spread across huge distances, the employees in these locations require a fast, secure and reliable way through which they can share private information with each other across the enterprise’s computer network. This network cannot be a public network for obvious reasons and this in turn means the enterprise now needs a private network to facilitate the smooth exchange of personal data and protection from cybercriminals.
Similarly, salespeople who have to work outside the office space too need a secure, reliable way so as to connect to their company’s computer network from remote locations. One of the ways of achieving this then is using a virtual private network (VPN).
What is a Virtual Private Network?
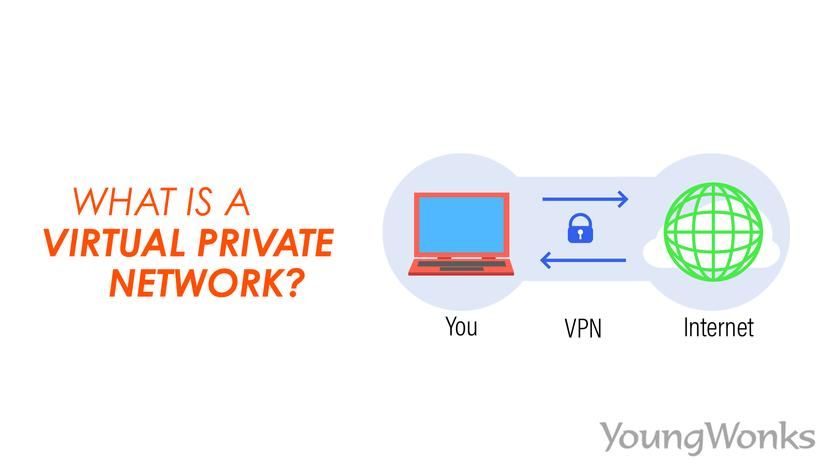
To put it simply, a virtual private network (VPN) is a private network that uses a public network - often the Internet - to connect remote users or sites together. The VPN, as the name says, makes use of virtual connections powered by the internet to connect the business’s private network or a third-party VPN service to the remote site or person.
So a VPN basically extends a private network across a public network, and allows users to send and receive data across shared or public networks. It protects one's IP address and online privacy by making an encrypted tunnel of sorts between your local network and an exit node in another place, even if it is several thousands of miles away. This in turn means online freedom, where one can easily get Internet access to certain apps and websites from that place even while on the go.
What’s equally important is that the date is being shared in a manner no different than if their computing devices were directly connected to the private network. This is why applications on computing devices - like laptops, desktops, iPads, mobile devices - can avail of the functionality, security, and management of the private network thanks to a VPN. VPNs also usually offer data encryption.
Here are the key benefits that a well-designed VPN connection offers:
- Extended connections across several geographic locations without using a leased line.
- Enhanced security for sharing data.
- Allows remote offices and employees the flexibility to use the business intranet over an existing internet connection as if they’re directly connected to the network.
- Time and expense saving for employees who needn’t commute to the office
Additionally, here are the basic features that a business VPN server must provide:
- Security: This will ensure that intruders trying to access the data are unable to read or use it.
- Reliability: Regardless of the location and the number of different locations, employees ought to be able to easily connect to the VPN at any time and access data that they need.
- Scalability: The availability of VPN services should not be impacted by an increase in the number of remote locations that need to be synced up.
Types of VPNs
The two main types of VPNs are the remote-access VPN and the site-to-site VPN.
Remote-access VPN
A remote-access VPN connects individual users in a secure fashion with a remote computer network. This is ideal for say, a company with hundreds of sales professionals working in the field as opposed to one office. Also called virtual private dial-up network (VPDN), it is a nod to its earliest form, a remote-access VPN that needed dialing in to a server using an analog telephone system.
One of the components needed in a remote-access VPN is the network access server (NAS). A NAS is what a user connects to from the Internet to be able to use a VPN; it can be a sole or one of many software applications running on a shared server. Users have to provide valid credentials to sign in to the VPN and the NAS uses its own authentication process or a separate authentication server running on the network.
Client software is the second component needed by remote-access VPNs. So employees who want to use the VPN from their computers need the software on those computers that can set up and maintain a connection to the VPN.
Large companies with their own IT teams usually buy, deploy and maintain their own remote-access VPNs.
Site-to-site VPN
A site-to-site VPN lets offices in many fixed locations set up secure connections with each other over a public network (the Internet). Site-to-site VPN basically expands the company’s network, making computer resources from one location available to employees in other locations.
There are two types of site-to-site VPNs:
Intranet-based VPN: This is when a company with one or more remote locations wants to join in a single private network and an intranet VPN is built to connect each separate LAN (local area network) to a single WAN (wide area network).
Extranet-based VPN: This is when a company joins in the network of another company -could be as a partner, supplier or customer. Here an extranet VPN connects the LANs of the two companies. Thus, an extranet VPN lets companies work together in a secure, shared network environment where there’s no access to their separate intranets.
Today there are many different VPN providers in the market and most paid VPN services work on all the major operating systems, including Microsoft Windows, Mac OS, Android, iOS and Linux.
How VPN works
This brings us to the question: how does a VPN work? How is it that it can keep our data secure? The answer lies in the fact that VPNs depend on tunneling to build a private network that spans across the Internet.
Tunneling is the process of housing one data packet within another packet before it's transmitted over the internet. That outer packet secures the contents from public view even as the packet moves within a virtual tunnel. The layering of data packets is called encapsulation.
Outgoing packets are encapsulated and incoming packets are reopened by computers - or other network devices - at the two ends of the tunnel. These devices are called tunnel interfaces. Users are typically at one end of the tunnel, while IT personnel are at one or both ends of the tunnel; together they configure the tunnel interfaces they are in charge of to use the tunneling protocol. It is important to note that every inner packet still has the passenger protocol, such as Internet protocol (IP), which determines how it travels on the LANs at each end of the tunnel.
Types of VPN protocols
Internet Protocol Security (IPSec)
A popular VPN protocol is the Internet Protocol Security, known as IPSec. It is used to ensure safe Internet communication across an IP network. It does so by verifying the session and encrypting each data packet during the connection.
IPSec runs in 2 modes:
(i) Transport mode
(ii) Tunneling mode
In the transport mode, the message in the data packet is encrypted and the whole data packet is encrypted in the tunneling mode. This protocol can be used with other security protocols to enhance the overall security.
Layer 2 Tunneling Protocol (L2TP)
L2TP or Layer 2 Tunneling Protocol is a tunneling protocol that is usually used along with another VPN security protocol like IPSec to set up a highly secure VPN connection. L2TP produces a tunnel between two L2TP connection points even as the IPSec protocol encrypts the data and maintains a safe line of communication in the tunnel.
Point–to–Point Tunneling Protocol (PPTP)
PPTP or Point-to-Point Tunneling Protocol is where a tunnel is built and the data packet is confined. Point-to-Point Protocol (PPP) is used to encrypt the data between the connections. A widely used VPN protocol, PPTP was earlier used on Windows and is today also used on Mac and Linux OSes.
SSL and TLS
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) produce a VPN connection where the web browser acts as the client and user cannot access certain applications instead of the entire network. Typically, these protocols are used by online shopping websites. SSL connections are indicated by the “https” in the initial of the URL instead of “http”.
Secure Shell (SSH)
Secure Shell or SSH produces the VPN tunnel for the data transfer while ensuring that the tunnel is encrypted. Data is basically transferred from a local port on to the remote server through the encrypted tunnel.
Open Source VPNs
While VPNs are certainly handy when it comes to browsing the internet anonymously and safely, open source VPNs (i.e. VPNs developed in a collaborative public fashion and typically released for free such that the copyright holder grants users the rights to use, study, change, and distribute the software and its source code to anyone and for any purpose) are suaully less vulnerable to hacking than the closed source (proprietary, non-free) VPNs. Not only do the former have greater reputations at stake but there's also the fact that all the source code of an open source VPN is public.
One of the biggest players among VPNs is OpenVPN, an open source VPN technology that comes with a 256-AES-CBC (AES here is short for Advanced Encryption Standard, a block cipher adopted as an encryption standard by the U.S. government and CBC stands for Cipher Blocker Chaining, an advanced form of block cipher encryption) with a 2048 bit Diffie-Hellman aka DH key (a method of securely exchanging cryptographic keys over a public channel) for Windows users. For Linux, iOS, and MacOS users, OpenVPN encrypts information using the IKEv2/IPsec protocol with an AES-256-CGM and 3072bit DH key.
VPN Applications
Today, VPN solutions are no longer being used just by businesses. Many people today are keen on securing their communications over unsecured public WiFi networks and those who wish to stay anonymous during their online transactions have now started subscribing to paid VPN services.
The fact of the matter is that a VPN can keep one’s computer, smartphone - and any other device one connects to the Internet - safe from hackers and malware. In fact, one may not need a firewall but instead a VPN will be more useful.
It also helps that these VPN services are quite easy to use. All one has to do is download the software, install it on one’s device, and connect to the server one picks. As long as your VPN is connected, no one (not even your Internet Service Provider aka ISP) can detect who you are, your location, or your online activity. Even if one is using public WiFi networks, a VPN can keep the connection secure and anonymous. This also means that when one travels, a VPN can help one gain access to geo-blocked websites and even streaming services such as Netflix, thus allowing one to view content from their home country.
Ideally one should be able to access the VPNs on all of one's devices as this will ensure complete protection. This means you’ll need a secure VPN on your phone, tablet, laptop, and desktop computer, which makes it an expensive proposition (if one is availing of a good quality paid VPN service). The smarter solution here would be installing VPN service on one's home or office router. This way, all appliances connected to the Internet through this router will be protected by the VPN.
Leading VPN service providers today include ExpressVPN, NordVPN (known for its top notch encryption), IPVanish for Android, CyberGhost for Mac and Hotspot Shield for Netflix.
Enhancing Internet Safety and Learning through VPNs
While exploring the concept of Virtual Private Networks (VPNs) and their importance in ensuring safe internet browsing, it's crucial for young learners and their guardians to be aware of the platforms where they can securely acquire technical knowledge. At Coding Classes for Kids, we're committed to providing a safe, engaging learning environment. For those interested in specific programming languages, our Python Coding Classes for Kids offer a solid foundation in one of the most versatile and popular languages today. Additionally, for students intrigued by hardware programming and game development, our courses on Raspberry Pi, Arduino and Game Development Coding Classes provide hands-on, project-based learning opportunities. By combining the security benefits of VPNs with structured learning pathways, we aim to foster a safe and enriching online educational experience.
*Contributors: Written by Vidya Prabhu; Lead image by: Leonel Cruz